How Digital Identity is Reshaping Online Privacy and Security
Billions upon billions of people in the world have been connected by the internet, which has provided the ability to access more and more information, services, and opportunities.
However, as the new connectivity grows, there are greater privacy, security, and data privacy concerns regarding how personal data is to be utilized. Digital identity solutions are trying to address these concerns by providing a more truthful identity to the internet’s consumers.
As digital identity systems mature, they will disrupt the world of online security and privacy as we know it. This article examines some of the key drivers and trends driving the the worldwide digital identity revolution, the risks and opportunities offered by such a change and what the future is likely to bring, with modern digital identities being used as passports into an increasingly digitized world.

The Evolution of Digital Identity
In this context, digital identity is the online credentials that we use to prove who we are so that we can interact with services, make transactions, exchange information, or with other people on the general internet. On top of that, this includes people’s usernames, passwords, security questions, biometrics like fingerprints or facial recognition — and other attributes that have made me unique and authentic online. The importance of digital identity has grown significantly as it plays a crucial role in ensuring secure and seamless interactions in the digital world.
Once upon a time, there were very basic digital identity systems based mostly on easy username and password credentials. While the complexity of our lives as we navigate our e-commerce, social media, cloud computing and mobile devices, the security and privacy threats have become proportionally more complex.
Some key events that have driven the evolution of digital ID:
- High-profile cyber attacks, like a breach of 3 billion Yahoo accounts in 2013, demonstrated vulnerabilities in existing authentication methods.
- Increased adoption of open authorization standards like OAuth and OpenID Connect aimed to make digital ID more portable and privacy-preserving.
- Data regulations like GDPR and CCPA gave users more control over their personal data, requiring strengthened consent and access management.
- The rise of blockchain, decentralization and self-sovereign identity introduced new models for managing digital ID without centralized intermediaries.
- Biometrics, AI, and advanced analytics have enabled more sophisticated identity-proofing and continuous authentication techniques.
- Digital ID pilot programs from governments and industry sought to improve identity verification and reduce fraud for essential services.
- The COVID-19 pandemic dramatically accelerated dependence on digital services, underscoring the need to enable remote access at scale.
These developments have set the stage for a new wave of digital identity solutions that put users at the center of addressing the rising privacy and security threats of the digital age.
Key Drivers Reshaping Digital Identity
Several interrelated technological and societal trends are driving rapid change in how digital identity and personal data are managed, both creating opportunities and risks for citizens, businesses and governments alike.
Complex and Fragmented Identity and Access Management
On average, the average internet user has 100 or more online accounts in a range of different types, including email, social media, apps, ecommerce and so on. It is a major security liability and inconvenient to juggle multiple usernames and passwords. In fact, more than 80 percent of data breaches are attributed to weak or stolen passwords. It is a must for modernizing identity and access management.
Emerging Data Regulations
In reaction to increasing data exploitation, Europe, Brazil, India, Japan, Thailand, and California have new data protection laws that protect users’ information and impose more control on them. Today, organizations are subject to increasing compliance requirements to collect consent, manage access, and demonstrate accountability for how data is used.
Increasing Use of Biometrics
Biometric identifiers such as fingerprints, face recognition, or iris scans give those personal identifiers far more security than you could achieve with passwords alone for authentication. More and more biometrics are being adopted across consumer devices, financial services, travel, and national ID.
Rise of Self-Sovereign Identity
Self-sovereign identity is hence referred to as user-centric or ‘by the user for the user’ identity with identity held by individuals rather than dependent on external authorities. Blockchain, encryption, and decentralization are enabled tools that create more privacy-preserving identities, which has become possible. The notion chimes in with a drive for greater consumer control of personal data use.
Digitization of Services due to COVID-19
Due to the coronavirus pandemic, digital transformation across industries happened rapidly during the pandemic. Schools, healthcare, government services and businesses suddenly went online.
To put it differently, while digital identity is beginning to emerge, these developments suggest a huge rewiring of not just how identities are likely to be managed but also how digital processes could be free of many centralized intermediaries. The implications cover access, trust, privacy, security, and, finally, the digital economy and citizens.
Emerging Technologies Reshaping Digital Identity
A number of pivotal technologies are converging to enable next-generation digital identity solutions focused on user control, privacy and decentralization.
Bitric-some
Revealing verified is a metaphor for biometrics defining a new realm of identity systems verifying users with their unique physical and behavioral attributes. We are seeing more and more mobile devices and financial services use such capabilities as fingerprint, facial, and voice recognition. High-security applications are evolving toward iris, vein and even DNA biometrics. The most resilient against spoofing multimodal systems are those that combine attributes. Biometrics allows one’s physical self to become the authentication credential.
Blockchain
Blockchain offers a decentralized and immutable ledger for storing and exchanging identity data across organizations. Through private key infrastructure, users maintain control rather than central authorities. Initiatives like Sovrin and Evernym leverage blockchain to create self-sovereign or user-managed identity networks. Decentralized identifiers (DIDs) anchored on blockchains are gaining support as the basis for the next-generation Internet of Trust.
Open Standards
Open standards are enabling interoperability for digital identity portability across domains. SAML, OpenID Connect and other open protocols allow identity federation between online services. W3C standards like Decentralized Identifiers (DIDs) and Verifiable Credentials facilitate user-centric identity capabilities. Adoption of common standards will be critical for widespread trust and acceptance.
Artificial Intelligence
AI and machine learning algorithms enable advanced identity proofing, authentication and predictive risk analysis. Dynamic biometrics can silently analyze keystroke patterns and other metrics to authenticate users during online sessions. AI-based risk engines can also more reliably detect sophisticated identity spoofing for stronger fraud prevention.
Edge Computing
Edge computing is pushing processing power to devices for faster yet privacy-preserving identity capabilities. Local processing prevents central data aggregation risks while enabling features like offline identity verification. Combined with biometrics, edge computing delivers authentication without reliance on external third parties – a key tenet of self-sovereign identity.
While technologies are pivotal, thought leadership around ethical frameworks, responsible design practices and change management will be equally vital to earning public trust and realizing digital identity’s transformative potential.
Opportunities: Why Digital Identity Matters
Implementing responsible digital identity solutions promises to simultaneously strengthen privacy protections, improve security and expand access to services – delivering profound economic and societal value.
Personal Privacy and Data Sovereignty
Digital identity gives the individual the power to decide how to identify herself and her personal information. In a decentralized model, third parties are subverted from the mass central aggregation of data to eliminate the risks of exploitation or abuse of the data. Selective disclosure features, fine-grained consent, and additional interoperability mechanisms serve to protect privacy while ensuring the reliability of credential portability from service to service.
Enhanced Security and Fraud Prevention
Biometric multi-factor authentication offers far stronger defenses against account takeovers or financial crime. It complicates the lives of attackers with expired single-factor passwords alone. However, this goes a bit further into continuous authentication, which is being enabled by AI and behavior analytics that validate the user identity passively throughout all digital sessions. Distributed ledgers also eliminate a single point of failure.
Financial Inclusion
The World Bank’s Identification for Development (ID4D) Global Dataset indicates that around 850 million people in the world do not have official identification as of 2021. It represents a large decrease from previous estimates of progress in global identification efforts. Because of this, digital identity promises to help access necessary services ethically.
Personalization and Seamless Experiences
Accurately verifying users with official credentials can achieve a more personalized experience and less friction. Single sign-on keeps devices from reauthenticating on various platforms. Based on your status, they can securely provide remote baggage services and check-ins. Customs pre-clearance can also expedite travel. In the world of online businesses, targeted identity verification increases conversions.
Civic Engagement and Voting Rights
Digital IDs could help protect voting rights. The Election Commission of India (ECI) has implemented various digital initiatives to enhance electoral participation, such as the Voter Helpline App. This app allows voters to verify their names in the electoral roll, register online, apply for corrections, download voter ID cards, and access real-time voter turnout data. Estonia allows online voting nationally using digital ID cards. Such capabilities widen democratic participation.
These opportunities demonstrate how thoughtfully implemented digital identity systems could make life online more secure, empowering and inclusive while supporting responsible innovation.
Risks and Challenges for the Digital Identity Revolution
While digital identity promises many upsides, without proper safeguards, several risks could emerge from mass adoption.
Privacy Erosion and Mass Surveillance
Centralized databases of personal identity data pose risks of abuse by corrupt insiders or via cyber attacks. Authenticating users across domains provides a holistic view of one’s activities that could enable mass surveillance. Mandating a single ID also removes alternatives that protect anonymity. Systems must be carefully designed to prevent central data aggregation.
Exclusion and Denial of Services
Strict identity requirements could exclude vulnerable groups like refugees, the mentally ill or the elderly who lack the capacity to obtain required credentials, thereby denying them vital services. Human review and exception handling must govern automated decision-making to prevent discrimination.
Vendor/Technology Lock-in
Portability is seen early in digital identity platforms, which remain siloed. Today, closed proprietary solutions lock users to specific technology vendors. Open standards and decentralized protocols, in general, play an important role in avoiding vendor-specific dependencies.
Scalability Challenges
Technical impediments to Aadhaar, India’s early national biometric ID scheme, including fingerprint authentication failures that excluded entitled beneficiaries, will have been seen by parties seeking data protection. This remains an open challenge in ensuring inclusive and reliable authentication at the population scale.
Cryptographic Weaknesses
Yet cryptography is secure in current days, but future developments could make old protocols ineffective. To avoid systemic failures, cryptography has to be planned to evolve over the long term.
In a proactively mitigating type of problem where risks get addressed before being realized, digital identity systems can responsibly come up with ways to strike a balance of both innovation and protection as they apply to citizens.
The Road Ahead: Future Outlook on Digital Identity
The digital identity landscape promises to evolve significantly in the years ahead with emerging trends that will shape adoption.
Mainstream Biometrics Adoption
Forrester predicts biometric authentication was mainstream across industries in the 2020s. Consumer comfort and demand for biometrics are rising, especially for fingerprint and facial recognition. Now, almost every device is equipped with this technology, and each of us uses biometrics to unlock our devices.
Blockchain-Based Identity Networks
Organizational identity networks are being built by such consortia as ID2020, Sovrin Foundation, and Trust over IP on open-source, blockchain-anchored organizational identity networks with user control. It is such an internet-scale trust layer for portable, self-sovereign credentials that can operate across industries and borders.
Convergence with IoT and Edge Computing
Statista forecasts there will be 39.6 billion connected IoT devices by 2033, enabling ambient identity capabilities.
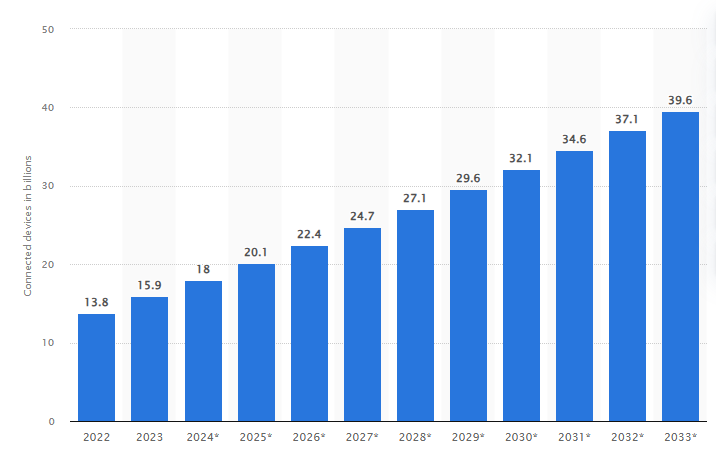
Edge computing will also minimize the risks of central data aggregation by only exchanging verification metadata rather than raw biometrics across systems. Together, IoT and edge computing promise seamless, consent-based identity lifecycle management.
Growth of Ethical Identity Frameworks
Responsible design practices for digital identity are coalescing around principles like inclusion, transparency, pluralism and non-discrimination, among others. The IEEE has developed one such foundational ethical framework to guide technical standards development and industry adoption. Further maturation of ethical governance will be imperative as adoption accelerates.
Role of AI and Advanced Analytics
AI will introduce new capabilities, from biometrics spoofing detection to predictive risk analysis and dynamic authentication patterns. Optimizing these algorithms for fairness, accountability and transparency will be critical to prevent automated bias. Explainable AI capabilities will enable human oversight safeguards around key decisions.
For those forecasting at the lower end of the curve, digital identity will accelerate, as in the case of open source and others, but things will reach a peak and then head downward. Open source was a change to proprietary systems, with freedom, versatility and trust. It was a gradual and irreversible disruption. Decentralization gave users more power than they had in closed, centralized systems.
Like self-sovereign identity networks, digital identity and service delivery are promised to change through the power of self-sovereignty. The technology returns power to the people over institutions by removing centralized intermediaries. But decentralized identity networks have to have common standards and global collaboration to grow to the scale of the Internet. Experts predict that if digital identity achieves its goal, it will follow the same path of open source and usher in a new paradigm of user empowerment — in the vein of personal computing and the Internet, once information access is liberated.
Conclusion
A key pillar of the new generation of the internet economy is the digital identity revolution. It could pave new opportunities and reshape online privacy, security and control by focusing on the solution principles of user control. However, bringing this vision to fruition will require some proactive efforts to ensure ethical practices, prevent exclusion, and build public trust.
Enabling people-centric digital identities can secure and control the consented exchange of information beyond the traditional identification document. This will promote economic inclusion, less friction in digital spaces and innovative services. To strike a delicate balance between convenience and robust protections, the stakeholders can develop a digital identity ecosystem based on transparency, interoperability, and user empowerment.
